A recent phishing campaign targeting Coinbase users shows thieves are getting cleverer about phishing one-time passwords (OTPs) needed to complete the login process. It also shows that phishers are attempting to sign up for new Coinbase accounts by the millions as part of an effort to identify email addresses that are already associated with active accounts.

A Google-translated version of the now-defunct Coinbase phishing site, coinbase.com.password-reset[.]com
Coinbase is the world’s second-largest cryptocurrency exchange, with roughly 68 million users from over 100 countries. The now-defunct phishing domain at issue — coinbase.com.password-reset[.]com — was targeting Italian Coinbase users (the site’s default language was Italian). And it was fairly successful, according to Alex Holden, founder of Milwaukee-based cybersecurity firm Hold Security.
Holden’s team managed to peer inside some poorly hidden file directories associated with that phishing site, including its administration page. That panel, pictured in the redacted screenshot below, indicated the phishing attacks netted at least 870 sets of credentials before the site was taken offline.
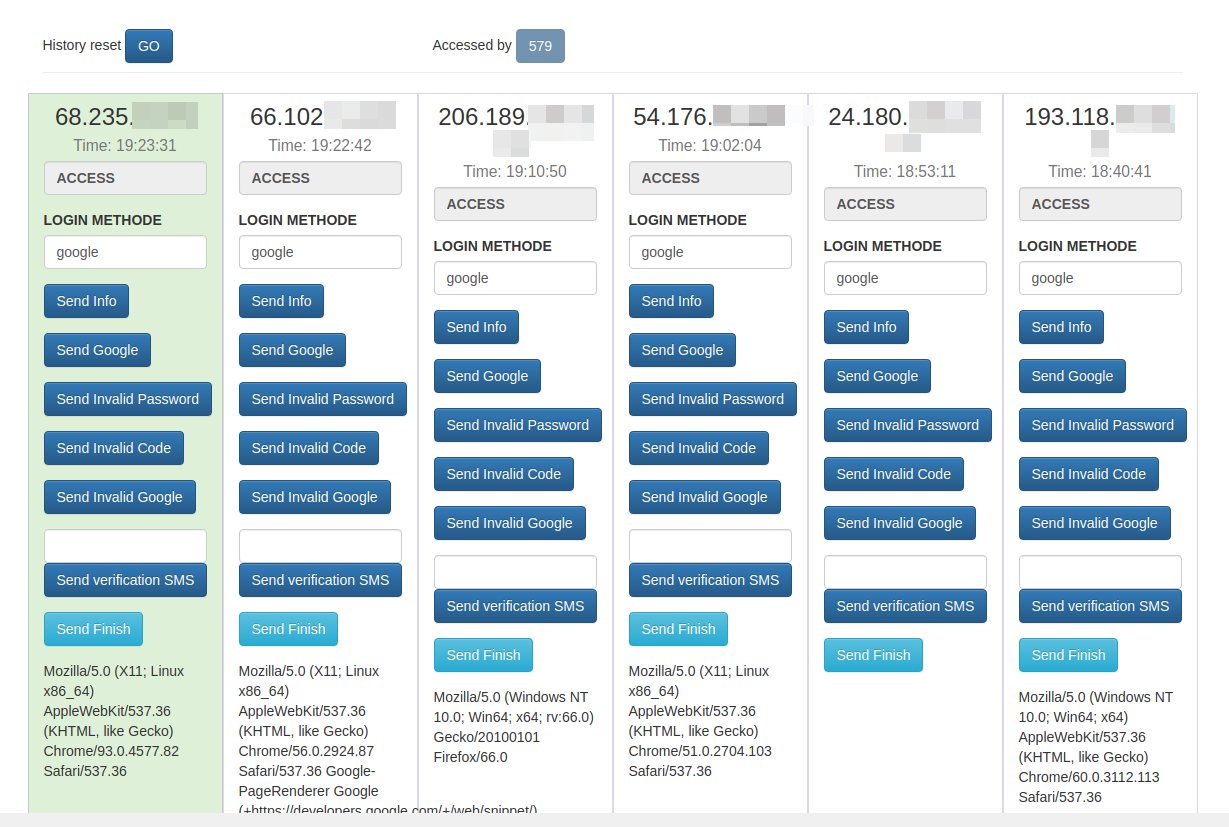
The Coinbase phishing panel.
Holden said each time a new victim submitted credentials at the Coinbase phishing site, the administrative panel would make a loud “ding” — presumably to alert whoever was at the keyboard on the other end of this phishing scam that they had a live one on the hook.
In each case, the phishers manually would push a button that caused the phishing site to ask visitors for more information, such as the one-time password from their mobile app.
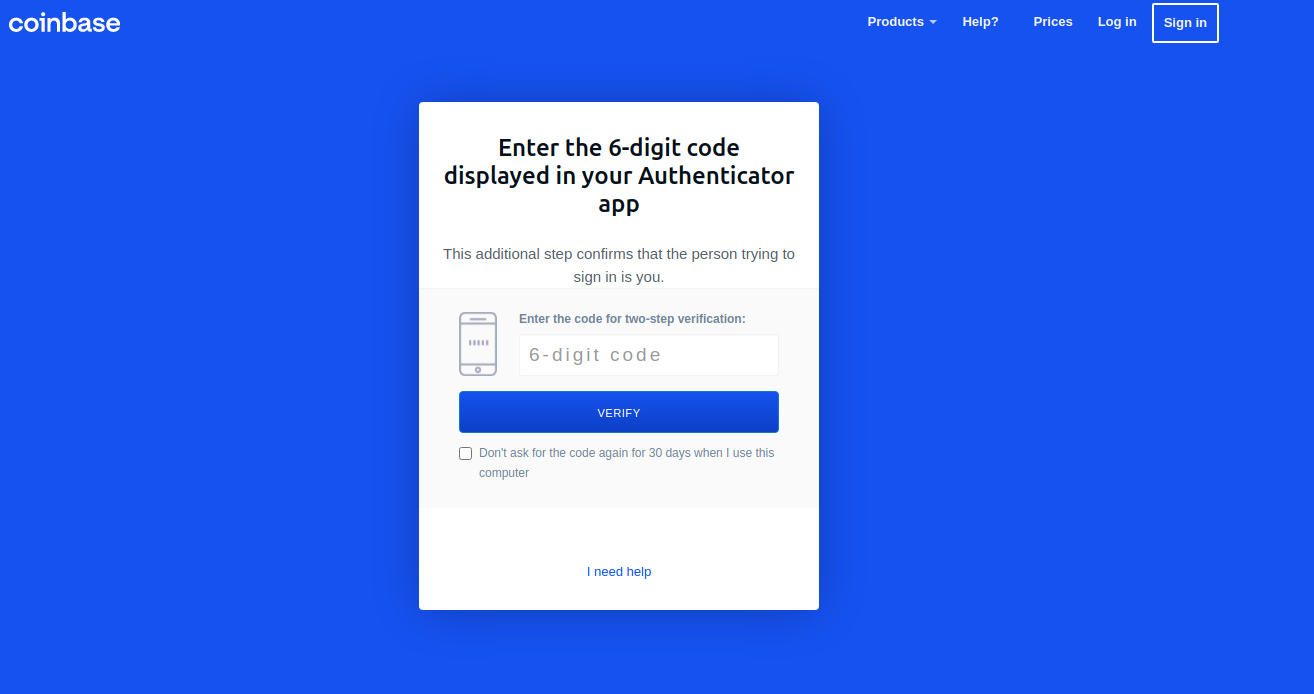
“These guys have real-time capabilities of soliciting any input from the victim they need to get into their Coinbase account,” Holden said.
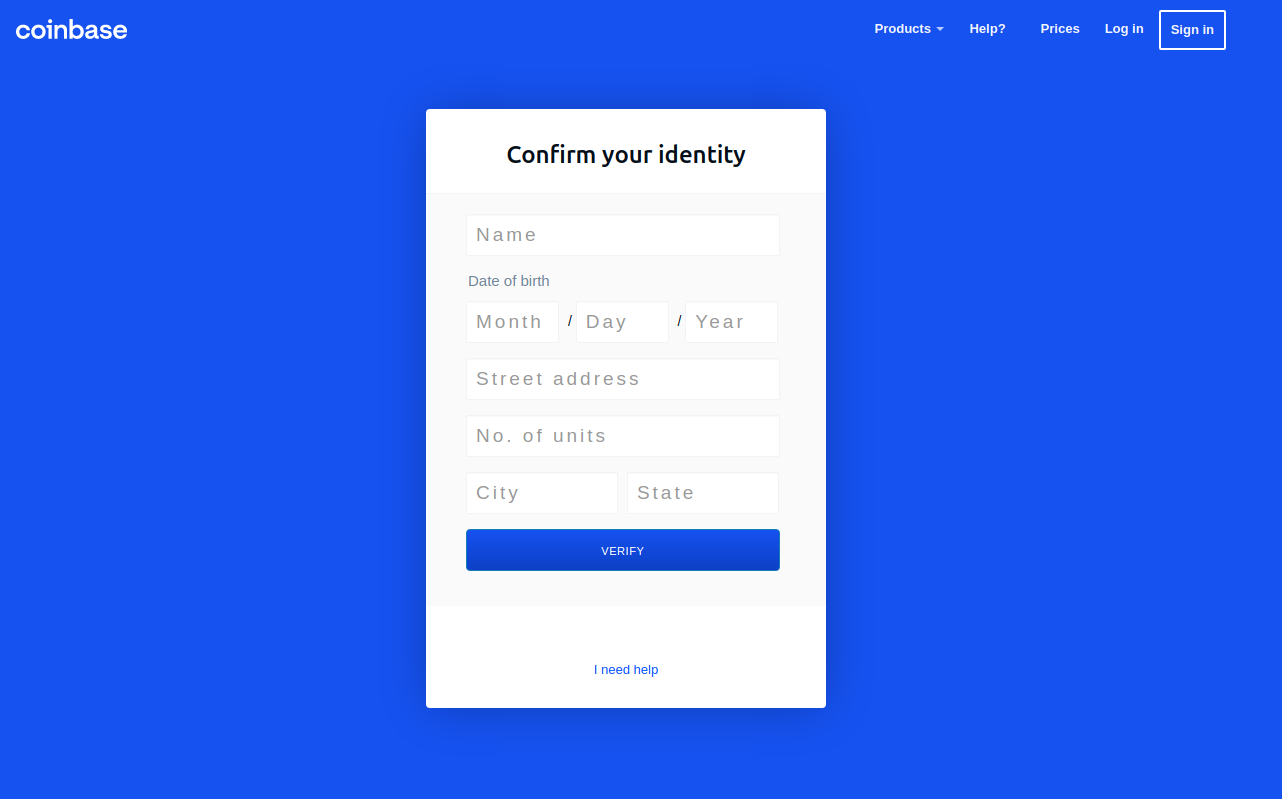
Pressing the “Send Info” button prompted visitors to supply additional personal information, including their name, date of birth, and street address. Armed with the target’s mobile number, they could also click “Send verification SMS” with a text message prompting them to text back a one-time code.
SIFTING COINBASE FOR ACTIVE USERS
Holden said the phishing group appears to have identified Italian Coinbase users by attempting to sign up new accounts under the email addresses of more than 2.5 million Italians. His team also managed to recover the username and password data that victims submitted to the site, and virtually all of the submitted email addresses ended in “.it”.
But the phishers in this case likely weren’t interested in registering any accounts. Rather, the bad guys understood that any attempts to sign up using an email address tied to an existing Coinbase account would fail. After doing that several million times, the phishers would then take the email addresses that failed new account signups and target them with Coinbase-themed phishing emails.
Holden’s data shows this phishing gang conducted hundreds of thousands of halfhearted account signup attempts daily. For example, on Oct. 10 the scammers checked more than 216,000 email addresses against Coinbase’s systems. The following day, they attempted to register 174,000 new Coinbase accounts.
In an emailed statement shared with KrebsOnSecurity, Coinbase said it takes “extensive security measures to ensure our platform and customer accounts remain as safe as possible.” Here’s the rest of their statement:
“Like all major online platforms, Coinbase sees attempted automated attacks performed on a regular basis. Coinbase is able to automatically neutralize the overwhelming majority of these attacks, using a mixture of in-house machine learning models and partnerships with industry-leading bot detection and abuse prevention vendors. We continuously tune these models to block new techniques as we discover them. Coinbase’s Threat Intelligence and Trust & Safety teams also work to monitor new automated abuse techniques, develop and apply mitigations, and aggressively pursue takedowns against malicious infrastructure. We recognize that attackers (and attack techniques) will continue to evolve, which is why we take a multi-layered approach to combating automated abuse.”
Last month, Coinbase disclosed that malicious hackers stole cryptocurrency from 6,000 customers after using a vulnerability to bypass the company’s SMS multi-factor authentication security feature.
“To conduct the attack, Coinbase says the attackers needed to know the customer’s email address, password, and phone number associated with their Coinbase account and have access to the victim’s email account,” Bleeping Computer’s Lawrence Abrams wrote. “While it is unknown how the threat actors gained access to this information, Coinbase believes it was through phishing campaigns targeting Coinbase customers to steal account credentials, which have become common.”
This phishing scheme is another example of how crooks are coming up with increasingly ingenious methods for circumventing popular multi-factor authentication options, such as one-time passwords. Last month, KrebsOnSecurity highlighted research into several new services based on Telegram-based bots that make it relatively easy for crooks to phish OTPs from targets using automated phone calls and text messages.These OTP phishing services all assume the customer already has the target’s login credentials through some means — such as through a phishing site like the one examined in this story.
Savvy readers here no doubt already know this, but to find the true domain referenced in a link, look to the right of “http(s)://” until you encounter the first slash (/). The domain directly to the left of that first slash is the true destination; anything that precedes the second dot to the left of that first slash is a subdomain and should be ignored for the purposes of determining the true domain name.
In the phishing domain at issue here — coinbase.com.password-reset[.]com — password-reset[.]com is the destination domain, and the “coinbase.com” is just an arbitrary subdomain of password-reset[.]com. However, when viewed in a mobile device, many visitors to such a domain may only see the subdomain portion of the URL in their mobile browser’s address bar.
The best advice to sidestep phishing scams is to avoid clicking on links that arrive unbidden in emails, text messages or other media. Most phishing scams invoke a temporal element that warns of dire consequences should you fail to respond or act quickly. If you’re unsure whether the message is legitimate, take a deep breath and visit the site or service in question manually — ideally, using a browser bookmark so as to avoid potential typosquatting sites.
Also, never provide any information in response to an unsolicited phone call. It doesn’t matter who claims to be calling: If you didn’t initiate the contact, hang up. Don’t put them on hold while you call your bank; the scammers can get around that, too. Just hang up. Then you can call your bank or wherever else you need.
By the way, when was the last time you reviewed your multi-factor settings and options at the various websites entrusted with your most precious personal and financial information? It might be worth paying a visit to 2fa.directory (formerly twofactorauth[.]org) for a checkup.