Breach at Sonic Drive-In May Have Impacted Millions of Credit, Debit Cards
mardi 26 septembre 2017 à 23:28Sonic Drive-In, a fast-food chain with nearly 3,600 locations across 45 U.S. states, has acknowledged a breach affecting an unknown number of store payment systems. The ongoing breach may have led to a fire sale on millions of stolen credit and debit card accounts that are now being peddled in shadowy underground cybercrime stores, KrebsOnSecurity has learned.

The first hints of a breach at Oklahoma City-based Sonic came last week when I began hearing from sources at multiple financial institutions who noticed a recent pattern of fraudulent transactions on cards that had all previously been used at Sonic.
I directed several of these banking industry sources to have a look at a brand new batch of some five million credit and debit card accounts that were first put up for sale on Sept. 18 in a credit card theft bazaar previously featured here called Joker’s Stash:
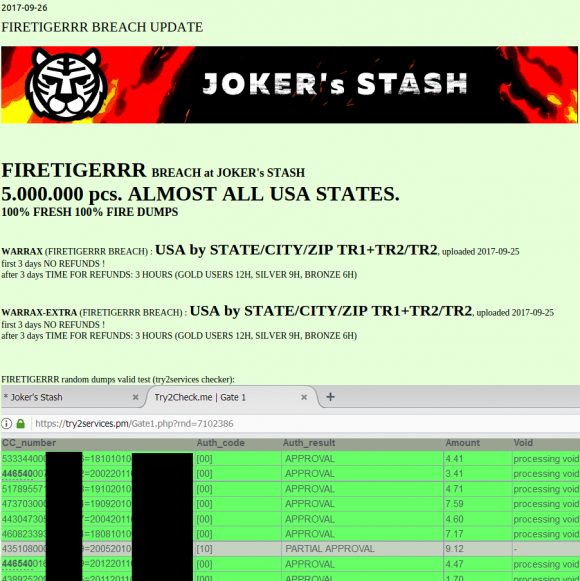
This batch of some five million cards put up for sale today (Sept. 26, 2017) on the popular carding site Joker’s Stash has been tied to a breach at Sonic Drive-In. The first batch of these cards appear to have been uploaded for sale on Sept. 15.
Sure enough, two sources who agreed to purchase a handful of cards from that batch of accounts on sale at Joker’s discovered they all had been recently used at Sonic locations.
Armed with this information, I phoned Sonic, which responded within an hour that it was indeed investigating “a potential incident” at some Sonic locations.
“Our credit card processor informed us last week of unusual activity regarding credit cards used at SONIC,” reads a statement the company issued to KrebsOnSecurity. “The security of our guests’ information is very important to SONIC. We are working to understand the nature and scope of this issue, as we know how important this is to our guests. We immediately engaged third-party forensic experts and law enforcement when we heard from our processor. While law enforcement limits the information we can share, we will communicate additional information as we are able.”
Christi Woodworth, vice president of public relations at Sonic, said the investigation is still in its early stages, and the company does not yet know how many or which of its stores may be impacted.
The accounts apparently stolen from Sonic are part of a batch of cards that Joker’s Stash is calling “Firetigerrr,” and they are indexed by city, state and ZIP code. This geographic specificity allows potential buyers to purchase only cards that were stolen from Sonic customers who live near them, thus avoiding a common anti-fraud defense in which a financial institution might block out-of-state transactions from a known compromised card.
Malicious hackers typically steal credit card data from organizations that accept cards by hacking into point-of-sale systems remotely and seeding those systems with malicious software that can copy account data stored on a card’s magnetic stripe. Thieves can use that data to clone the cards and then use the counterfeits to buy high-priced merchandise from electronics stores and big box retailers.
Prices for the cards advertised in the Firetigerr batch are somewhat higher than for cards stolen in other breaches, likely because this batch is extremely fresh and unlikely to have been canceled by card-issuing banks yet.
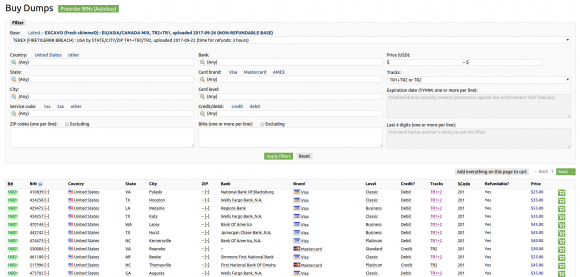
Dumps available for sale on Joker’s Stash from the “FireTigerrr” base, which has been linked to a breach at Sonic Drive-In. Click image to enlarge.
Most of the cards range in price from $25 to $50, and the price is influenced by a number of factors, including: the type of card issued (Amex, Visa, MasterCard, etc); the card’s level (classic, standard, signature, platinum, etc.); whether the card is debit or credit; and the issuing bank.
I should note that it remains unclear whether Sonic is the only company whose customers’ cards are being sold in this particular batch of five million cards at Joker’s Stash. There are some (as yet unconfirmed) indications that perhaps Sonic customer cards are being mixed in with those stolen from other eatery brands that may be compromised by the same attackers.
The last known major card breach involving a large nationwide fast-food chain impacted more than a thousand Wendy’s locations and persisted for almost nine months after it was first disclosed here. The Wendy’s breach was extremely costly for card-issuing banks and credit unions, which were forced to continuously re-issue customer cards that kept getting re-compromised every time their customers went back to eat at another Wendy’s.
Part of the reason Wendy’s corporate offices had trouble getting a handle on the situation was that most of the breached locations were not corporate-owned but instead independently-owned franchises whose payment card systems were managed by third-party point-of-sale vendors.
According to Sonic’s Wikipedia page, roughly 90 percent of Sonic locations across America are franchised.
Dan Berger, president and CEO of the National Association of Federally Insured Credit Unions, said he’s not looking forward to the prospect of another Wendy’s-like fiasco.
“It’s going to be the financial institution that makes them whole, that pays off the charges or replaces money in the customer’s checking account, or reissues the cards, and all those costs fall back on the financial institutions,” Berger said. “These big card breaches are going to continue until there’s a national standard that holds retailers and merchants accountable.”
Financial institutions also bear some of the blame for the current state of affairs. The United States is embarrassingly the last of the G20 nations to make the shift to more secure chip-based cards, which are far more expensive and difficult for criminals to counterfeit. But many financial institutions still haven’t gotten around to replacing traditional magnetic stripe cards with chip-based cards. According to Visa, 58 percent of the more than 421 million Visa cards issued by U.S. financial institutions were chip-based as of March 2017.
Likewise, retailers that accept chip cards may present a less attractive target to hackers than those that don’t. In March 2017, Visa said the number of chip-enabled merchant locations in the country reached two million, representing 44 percent of stores that accept Visa.