Expect Phishers to Up Their Game in 2016
mercredi 23 décembre 2015 à 07:49Expect phishers and other password thieves to up their game in 2016: Both Google and Yahoo! are taking steps to kill off the password as we know it.
 New authentication methods now offered by Yahoo! and to a beta group of Google users let customers log in just by supplying their email address, and then responding to a notification sent to their mobile device.
New authentication methods now offered by Yahoo! and to a beta group of Google users let customers log in just by supplying their email address, and then responding to a notification sent to their mobile device.
According to TechCrunch, Google is giving select Gmail users a password-free means of signing in. It uses a “push” notification sent to your phone that then opens an app where you approve the log-in.
The article says the service Google is experimenting with will let users sign in without entering a password, but that people can continue to use their typed password if they choose. It also says Google may still ask for your password as an additional security measure if it notices anything unusual about a login attempt.
The new authentication feature being tested by some Gmail users comes on the heels of a similar service Yahoo! debuted in October 2015. That offering, called “on-demand passwords,” will text users a random four-character code (the ones I saw were all uppercase letters) that needs to be entered into a browser or mobile device.
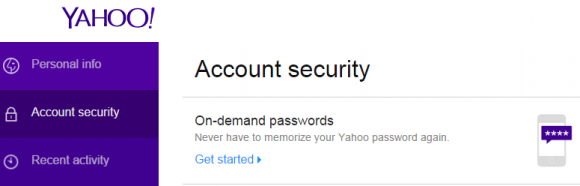
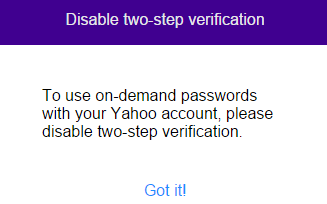
This is not Yahoo!’s first stab at two-factor authentication. Another security feature it has offered for years — called “two-step verification” — sends a security code to your phone when you log in from new devices, but only after you supply your password. Yahoo! users who wish to take advantage of the passwords-free, on-demand password feature will need to disable two-step verification for on-demand passwords to work.
Yahoo! also warns that some non-Yahoo apps like Apple mail and Outlook won’t work. For those programs to access your Yahoo! mail with on-demand passwords enabled, you’ll need to set up app-specific passwords. Yahoo! provides instructions on how to do that here.
The system that Google is reportedly beta testing sounds easier to use, and more like true two-factor authentication. It doesn’t require the user to enter any code, and he just has to click a button on an app that tells the login to proceed.
All of this had me wondering: Should we expect Microsoft to roll out a similar password-free login process for Hotmail or Outlook users? It doesn’t seem likely: A spokesperson for the company referred me to Microsoft’s Passport system, which also uses a password-free authentication system. However, Passport’s key two-factor features are only available to Windows 10 users.
To come full circle on the lead of this story, I think it’s likely we’ll see an increase in more targeted, personalized phishing attacks if Google and Yahoo!’s two-factor solutions gain wide adoption. Perhaps Google anticipated this in April 2015, when it starting offering its Password Alert feature — a Google Chrome browser add-on that will display a warning if you type your Google password into a site that isn’t a Google sign-in page. Google says this protects users from phishing attacks and also encourages people to use different passwords for different sites, a security best practice.
Plenty of other online services now offer two-step authentication. Twofactorauth.org has a fairly comprehensive breakdown of those that do and don’t. Consider dropping by there to see if you’re taking full advantage of all of the security offered for your various online accounts.
 The FTC sued Oracle over years of failing to remove older, more vulnerable versions of Java SE when consumers updated their systems to the newest Java software. Java is installed on more than 850 million computers, but only recently (in Aug. 2014) did the company change its updater software to reliably remove older versions of Java during the installation process.
The FTC sued Oracle over years of failing to remove older, more vulnerable versions of Java SE when consumers updated their systems to the newest Java software. Java is installed on more than 850 million computers, but only recently (in Aug. 2014) did the company change its updater software to reliably remove older versions of Java during the installation process.
 Mountain View, Calif. based Gyft lets customers buy and use gift cards entirely from their mobile devices. Acting on a tip from a trusted source in the cybercrime underground who reported that a cache of account data on Gyft customers was on offer for the right bidder, KrebsOnSecurity contacted Gyft to share intelligence and to request comment.
Mountain View, Calif. based Gyft lets customers buy and use gift cards entirely from their mobile devices. Acting on a tip from a trusted source in the cybercrime underground who reported that a cache of account data on Gyft customers was on offer for the right bidder, KrebsOnSecurity contacted Gyft to share intelligence and to request comment.
