Govt. Cybersecurity Contractor Hit in W-2 Phishing Scam
vendredi 17 mars 2017 à 23:02Just a friendly reminder that phishing scams which spoof the boss and request W-2 tax data on employees are intensifying as tax time nears. The latest victim shows that even cybersecurity experts can fall prey to these increasingly sophisticated attacks.
 On Thursday, March 16, the CEO of Defense Point Security, LLC — a Virginia company that bills itself as “the choice provider of cyber security services to the federal government” — told all employees that their W-2 tax data was handed directly to fraudsters after someone inside the company got caught in a phisher’s net.
On Thursday, March 16, the CEO of Defense Point Security, LLC — a Virginia company that bills itself as “the choice provider of cyber security services to the federal government” — told all employees that their W-2 tax data was handed directly to fraudsters after someone inside the company got caught in a phisher’s net.
Alexandria, Va.-based Defense Point Security (recently acquired by management consulting giant Accenture) informed current and former employees this week via email that all of the data from their annual W-2 tax forms — including name, Social Security Number, address, compensation, tax withholding amounts — were snared by a targeted spear phishing email.
“I want to alert you that a Defense Point Security (DPS) team member was the victim of a targeted spear phishing email that resulted in the external release of IRS W-2 Forms for individuals who DPS employed in 2016,” Defense Point CEO George McKenzie wrote in the email alert to employees. “Unfortunately, your W-2 was among those released outside of DPS.”
W-2 scams start with spear phishing emails usually directed at finance and HR personnel. The scam emails will spoof a request from the organization’s CEO (or someone similarly high up in the organization) and request all employee W-2 forms.
Defense Point did not return calls or emails seeking comment. An Accenture spokesperson issued the following brief statement: “Data protection and our employees are top priorities. Our leadership and security team are providing support to all impacted employees.”
The email that went out to Defense Point employees Thursday does not detail when this incident occurred, to whom the information was sent, or how many employees were impacted. But a review of information about the company on LinkedIn suggests the breach letter likely was sent to around 200 to 300 employees nationwide (if we count past employees also).
Among Defense Point’s more sensitive projects is the U.S. Immigration and Customs Enforcement (ICE) Security Operations Center (SOC) based out of Phoenix, Ariz. That SOC handles cyber incident response, vulnerability mitigation, incident handling and cybersecurity policy enforcement for the agency.
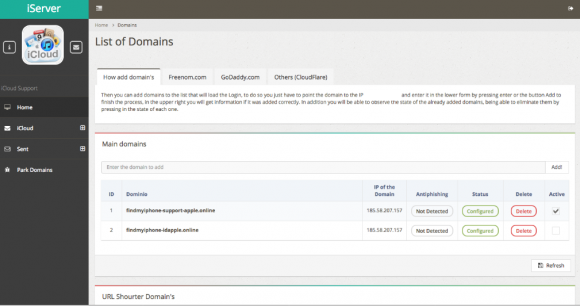
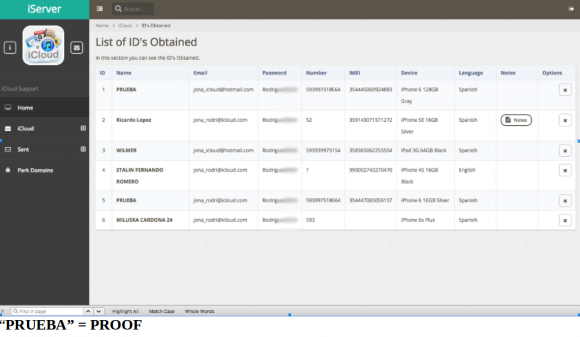
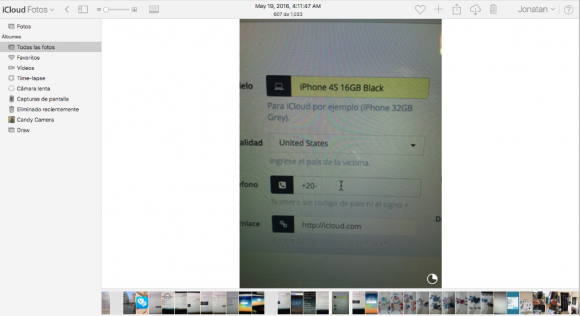
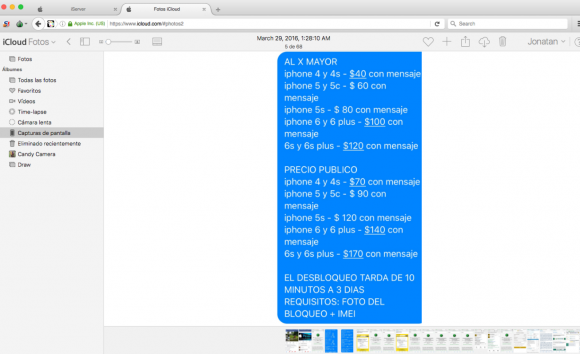
Fraudsters who perpetrate tax refund fraud prize W-2 information because it contains virtually all of the data one would need to fraudulently file someone’s taxes and request a large refund in their name. Scammers in tax years past also have massively phished online payroll management account credentials used by corporate HR professionals. This year, they are going after people who run tax preparation firms, and W-2’s are now being openly sold in underground cybercrime stores.
Tax refund fraud affects hundreds of thousands, if not millions, of U.S. citizens annually. Victims usually first learn of the crime after having their returns rejected because scammers beat them to it. Even those who are not required to file a return can be victims of refund fraud, as can those who are not actually due a refund from the IRS.
ANALYSIS
I find it interesting that a company which obviously handles extremely sensitive data on a regular basis and one that manages a highly politicized government agency would not anticipate such attacks and deploy some kind of data-loss prevention (DLP) technology to stop sensitive information from leaving their networks.
Thanks to their mandate as an agency, ICE is likely a high risk target for hacktivists and nation-state hackers. This was not a breach in which data was exfiltrated through stealthy means; the tax data was sent by an employee openly through email. This suggests that either there were no DLP technical controls active in their email environment, or they were inadequately configured to prevent information in SSN format from leaving the network.
This incident also suggests that perhaps Defense Point does not train their employees adequately in information security, and yet they are trusted to maintain the security environment for a major government agency. This from a company that sells cybersecurity education and training as a service to others.
DON’T BE THE NEXT VICTIM
While there isn’t a great deal you can do to stop someone at your employer from falling for one of these W-2 phishing scams, here are some steps you can take to make it less likely that you will be the next victim of tax refund fraud:
-File before the fraudsters do it for you – Your primary defense against becoming the next victim is to file your taxes at the state and federal level as quickly as possible. Remember, it doesn’t matter whether or not the IRS owes you money: Thieves can still try to impersonate you and claim that they do, leaving you to sort out the mess with the IRS later.
-Get on a schedule to request a free copy of your credit report. By law, consumers are entitled to a free copy of their report from each of the major bureaus once a year. Put it on your calendar to request a copy of your file every three to four months, each time from a different credit bureau. Dispute any unauthorized or suspicious activity. This is where credit monitoring services are useful: Part of their service is to help you sort this out with the credit bureaus, so if you’re signed up for credit monitoring make them do the hard work for you.
-File form 14039 and request an IP PIN from the government. This form requires consumers to state they believe they’re likely to be victims of identity fraud. Even if thieves haven’t tried to file your taxes for you yet, virtually all Americans have been touched by incidents that could lead to ID theft — even if we just look at breaches announced in the past year alone.
–Consider placing a “security freeze” on one’s credit files with the major credit bureaus. See this tutorial about why a security freeze — also known as a “credit freeze,” may be more effective than credit monitoring in blocking ID thieves from assuming your identity to open up new lines of credit. While it’s true that having a security freeze on your credit file won’t stop thieves from committing tax refund fraud in your name, it would stop them from fraudulently obtaining your IP PIN.
–Monitor, then freeze. Take advantage of any free credit monitoring available to you, and then freeze your credit file with the four major bureaus. Instructions for doing that are here.

![An advertisement for the carding shop “briansdump[dot]ru” promotes “dumps from the legendary Brian Krebs.” Needless to say, this is not an endorsed site.](./media/15df5c65.briansdumps.png)


 Microsoft’s
Microsoft’s  The smartest option is probably to ditch the program once and for all and significantly increase the security of your system in the process. An extremely powerful and buggy program that binds itself to the browser, Flash is a favorite target of attackers and malware. For some ideas about how to hobble or do without Flash (as well as slightly less radical solutions) check out
The smartest option is probably to ditch the program once and for all and significantly increase the security of your system in the process. An extremely powerful and buggy program that binds itself to the browser, Flash is a favorite target of attackers and malware. For some ideas about how to hobble or do without Flash (as well as slightly less radical solutions) check out