If you’ve been paying attention in recent years, you might have noticed that just about everyone is losing your personal data. Even if you haven’t noticed (or maybe you just haven’t actually received a breach notice), I’m here to tell you that if you’re an American, your basic personal data is already for sale. What follows is a primer on what you can do to avoid becoming a victim of identity theft as a result of all this data (s)pillage.

Click here for a primer on identity theft protection services.
A seemingly never-ending stream of breaches at banks, healthcare providers, insurance companies and data brokers has created a robust market for thieves who sell identity data. Even without the help of mega breaches like the 80 million identities leaked in the Anthem compromise or last week’s news about 4 million records from the U.S. Office of Personnel Management gone missing, crooks already have access to the information needed to open new lines of credit or file phony tax refund requests in your name.
If your response to this breachapalooza is to do what each of the breached organizations suggest — to take them up on one or two years’ worth of free credit monitoring services — you might sleep better at night but you will probably not be any more protected against crooks stealing your identity. As I discussed at length in this primer, credit monitoring services aren’t really built to prevent ID theft. The most you can hope for from a credit monitoring service is that they give you a heads up when ID theft does happen, and then help you through the often labyrinthine process of getting the credit bureaus and/or creditors to remove the fraudulent activity and to fix your credit score.
In short, if you have already been victimized by identity theft (fraud involving existing credit or debit cards is not identity theft), it might be worth paying for these credit monitoring and repair services (although more than likely, you are already eligible for free coverage thanks to a recent breach at any one of dozens of companies that have lost your information over the past year). Otherwise, I’d strongly advise you to consider freezing your credit file at the major credit bureaus.
There is shockingly little public knowledge or education about the benefits of a security freeze, also known as a “credit freeze.” I routinely do public speaking engagements in front of bankers and other experts in the financial industry, and I’m amazed at how often I hear from people in this community who are puzzled to learn that there is even such a thing as a security freeze (to be fair, most of these people are in the business of opening new lines of credit, not blocking such activity).
Also, there is a great deal of misinformation and/or bad information about security freezes available online. As such, I thought it best to approach this subject in the form of a Q&A, which is the most direct method I know how to impart knowledge about a subject in way that is easy for readers to digest.
Q: What is a security freeze?
A: A security freeze essentially blocks any potential creditors from being able to view or “pull” your credit file, unless you affirmatively unfreeze or thaw your file beforehand. With a freeze in place on your credit file, ID thieves can apply for credit in your name all they want, but they will not succeed in getting new lines of credit in your name because few if any creditors will extend that credit without first being able to gauge how risky it is to loan to you (i.e., view your credit file). And because each credit inquiry caused by a creditor has the potential to lower your credit score, the freeze also helps protect your score, which is what most lenders use to decide whether to grant you credit when you truly do want it and apply for it.
Q: What’s involved in freezing my credit file?
A: Freezing your credit involves notifying each of the major credit bureaus that you wish to place a freeze on your credit file. This can usually be done online, but in a few cases you may need to contact one or more credit bureaus by phone or in writing. Once you complete the application process, each bureau will provide a unique personal identification number (PIN) that you can use to unfreeze or “thaw” your credit file in the event that you need to apply for new lines of credit sometime in the future. Depending on your state of residence and your circumstances, you may also have to pay a small fee to place a freeze at each bureau. There are four consumer credit bureaus, including Equifax, Experian, Innovis and Trans Union.
Q: How much is the fee, and how can I know whether I have to pay it?
A: The fee ranges from $0 to $15 per bureau, meaning that it can cost upwards of $60 to place a freeze at all four credit bureaus (recommended). However, in most states, consumers can freeze their credit file for free at each of the major credit bureaus if they also supply a copy of a police report and in some cases an affidavit stating that the filer believes he/she is or is likely to be the victim of identity theft. In many states, that police report can be filed and obtained online. The fee covers a freeze as long as the consumer keeps it in place. Equifax has a decent breakdown of the state laws and freeze fees/requirements.
Q: What’s involved in unfreezing my file?
A: The easiest way to unfreeze your file for the purposes of gaining new credit is to spend a few minutes on the phone with the company from which you hope to gain the line of credit (or perhaps research the matter online) to see which credit bureau they rely upon for credit checks. It will most likely be one of the major bureaus. Once you know which bureau the creditor uses, contact that bureau either via phone or online and supply the PIN they gave you when you froze your credit file with them. The thawing process should not take more than 24 hours.
Q: I’ve heard about something called a fraud alert. What’s the difference between a security freeze and a fraud alert on my credit file?
A: With a fraud alert on your credit file, lenders or service providers should not grant credit in your name without first contacting you to obtain your approval — by phone or whatever other method you specify when you apply for the fraud alert. To place a fraud alert, merely contact one of the credit bureaus via phone or online, fill out a short form, and answer a handful of multiple-choice, out-of-wallet questions about your credit history. Assuming the application goes through, the bureau you filed the alert with must by law share that alert with the other bureaus.
Consumers also can get an extended fraud alert, which remains on your credit report for seven years. Like the free freeze, an extended fraud alert requires a police report or other official record showing that you’ve been the victim of identity theft.
An active duty alert is another alert available if you are on active military duty. The active duty alert is similar to an initial fraud alert except that it lasts 12 months and your name is removed from pre-approved firm offers of credit or insurance (prescreening) for 2 years.
Q: Why would I pay for a security freeze when a fraud alert is free?
A: Fraud alerts only last for 90 days, although you can renew them as often as you like. More importantly, while lenders and service providers are supposed to seek and obtain your approval before granting credit in your name if you have a fraud alert on your file, they’re not legally required to do this.
Q: Hang on: If I thaw my credit file after freezing it so that I can apply for new lines of credit, won’t I have to pay to refreeze my file at the credit bureau where I thawed it?
A: Yes (unless you’ve previously qualified for a free freeze). However, even if you have to do this once or twice a year, the cost of doing so is almost certainly less than paying for a year’s worth of credit monitoring services.
Q: Is there anything I should do in addition to placing a freeze that would help me get the upper hand on ID thieves?
A: Yes: Periodically order a free copy of your credit report. By law, each of the three major credit reporting bureaus must provide a free copy of your credit report each year — via a government-mandated site: annualcreditreport.com. The best way to take advantage of this right is to make a notation in your calendar to request a copy of your report every 120 days, to review the report and to report any inaccuracies or questionable entries when and if you spot them.
Q: I’ve heard that tax refund fraud is a big deal now. Would having a fraud alert or security freeze prevent thieves from filing phony tax refund requests in my name with the states and with the Internal Revenue Service?
A: Neither would stop thieves from fraudulently requesting a refund in your name. However, a freeze on your credit file would have prevented thieves from using the IRS’s own Web site to request a copy of your previous year’s tax transcript — a problem the IRS said led to tax fraud on 100,000 Americans this year and that prompted the agency to suspend online access to the information. For more information on what you can do to minimize your exposure to tax refund fraud, see this primer.
Q: Okay, I’ve got a security freeze on my file, what else should I do?
A: It’s also a good idea to notify a company called ChexSystems to keep an eye out for fraud committed in your name. Thousands of banks rely on ChexSystems to verify customers that are requesting new checking and savings accounts, and ChexSystems lets consumers place a security alert on their credit data to make it more difficult for ID thieves to fraudulently obtain checking and savings accounts. For more information on doing that with ChexSystems, see this link.
Q: If I freeze my file, won’t I have trouble getting new credit going forward?
A: If you’re in the habit of applying for a new credit card each time you see a 10 percent discount for shopping in a department store, a security freeze may cure you of that impulse. Other than that, as long as you already have existing lines of credit (credit cards, loans, etc) the credit bureaus should be able to continue to monitor and evaluate your creditworthiness should you decide at some point to take out a new loan or apply for a new line of credit.
Q: Anything else?
A: ID thieves like to intercept offers of new credit and insurance sent via postal mail, so it’s a good idea to opt out of pre-approved credit offers. If you decide that you don’t want to receive prescreened offers of credit and insurance, you have two choices: You can opt out of receiving them for five years or opt out of receiving them permanently.
To opt out for five years: Call toll-free 1-888-5-OPT-OUT (1-888-567-8688) or visit www.optoutprescreen.com. The phone number and website are operated by the major consumer reporting companies.
To opt out permanently: You can begin the permanent Opt-Out process online at www.optoutprescreen.com. To complete your request, you must return the signed Permanent Opt-Out Election form, which will be provided after you initiate your online request.
PERSONAL EXPERIENCE
A couple of years back, I was signed up for a credit monitoring service and had several unauthorized applications for credit filed in my name in rapid succession. Over a period of weeks, I fielded numerous calls from the credit monitoring firm, and spent many grueling hours on the phone with the firm’s technicians and with the banks that had been tricked into granting the credit — all in a bid to convince the latter that I had not in fact asked them for a new credit line.
The banks in question insisted that I verify my identity by giving them all of my personal information that they didn’t already have, and I was indignant that they should have been that careful before opening the new fraudulent accounts. Needless to say, the experience was extremely frustrating and massively time-consuming.
We eventually got that straightened out, but it took weeks. Not long after that episode, I decided to freeze my credit and that of my wife’s at all of the major bureaus. Turns out, I did that none too soon: A few weeks later, I broke a story about a credit card breach at nationwide beauty chain Sally Beauty, detailing how the cards stolen from Sally Beauty customers had wound up for sale on Rescator[dot]cc, the same fraud shop that had been principally responsible for selling cards stolen in the wake of the massive data breaches at Home Depot and Target.
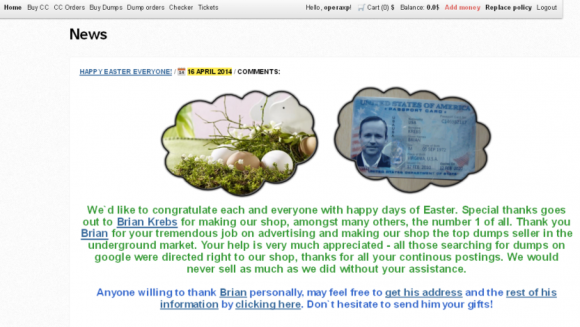
Rescator’s message to his customers urging them to steal my identity.
In response to my reporting about him and his site, Rescator changed his site’s home page to a photoshopped picture of my driver’s license, and linked his customers (mostly identity thieves and credit card hustlers) to a full copy of my credit report along with links to dozens of sites where one can apply for instant credit. Rescator also encouraged his friends and customers to apply for new credit in my name.
Over the next few weeks, I received multiple rejection letters from various financial firms, stating that although they had hoped to be able to grant my application for new credit, they were unable to do so because they could not view my credit file. The freeze had done its job.
In summary, credit monitoring services are helpful in digging you out of an identity theft ditch. But if you want true piece of mind, freeze your credit file.
 The bulk of the flaws Microsoft addressed today (23 of them) reside in the Internet Explorer Web browser. Microsoft also issued fixes for serious problems in Office, the Windows OS itself and Windows Media Player, among other components. A link to an index of the individual Microsoft updates released today is here.
The bulk of the flaws Microsoft addressed today (23 of them) reside in the Internet Explorer Web browser. Microsoft also issued fixes for serious problems in Office, the Windows OS itself and Windows Media Player, among other components. A link to an index of the individual Microsoft updates released today is here.





