SpamHaus, CloudFlare Attacker Pleads Guilty
dimanche 14 décembre 2014 à 04:55A 17-year-old male from London, England pleaded guilty this week to carrying out a massive denial-of-service attack last year against anti-spam outfit SpamHaus and content delivery network CloudFlare, KrebsOnSecurity has learned.
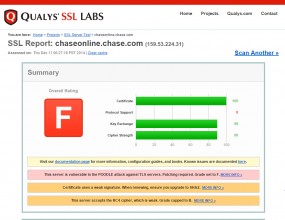
 In late March 2013, a massive distributed denial-of-service (DDoS) attack hit the web site of SpamHaus, an organization that distributes a blacklist of spammers to email and network providers. When SpamHaus moved its servers behind CloudFlare, which specializes in blocking such attacks — the attackers pelted CloudFlare’s network. The New York Times called the combined assault the largest known DDoS attack ever on the Internet at the time; for its part, CloudFlare dubbed it “the attack that almost broke the Internet.”
In late March 2013, a massive distributed denial-of-service (DDoS) attack hit the web site of SpamHaus, an organization that distributes a blacklist of spammers to email and network providers. When SpamHaus moved its servers behind CloudFlare, which specializes in blocking such attacks — the attackers pelted CloudFlare’s network. The New York Times called the combined assault the largest known DDoS attack ever on the Internet at the time; for its part, CloudFlare dubbed it “the attack that almost broke the Internet.”
In April 2013, an unnamed then-16-year-old male from London identified only by his hacker alias “Narko,” was arrested and charged with computer misuse and money laundering in connection with the attack.
Sources close to the investigation now tell KrebsOnSecurity that Narko has pleaded guilty to those charges, and that Narko’s real name is Sean Nolan McDonough. A spokesman for the U.K. National Crime Agency confirmed that a 17-year-old male from London had pleaded guilty to those charges on Dec. 10, but noted that “court reporting restrictions are in place in respect to a juvenile offender, [and] as a consequence the NCA will not be releasing further detail.”
During the assault on SpamHaus, Narko was listed as one of several moderators of the forum Stophaus[dot]com, a motley crew of hacktivists, spammers and bulletproof hosting providers who took credit for organizing the attack on SpamHaus and CloudFlare.
WHO RUNS STOPHAUS?
It is likely that McDonough/Narko was hired by someone else to conduct the attack. So, this seems as good a time as any to look deeper into who’s likely the founder and driving force behind the Stophaus movement itself. All signs point to an angry, failed spammer living in Florida who runs an organization that calls itself the Church of Common Good.
 Not long after McDonough’s arrest, a new Facebook page went online called “Freenarko,” which listed itself as “a solidarity support group to help in the legal defense and media stability for ‘Narko,’ a 16-yr old brother in London who faces charges concerning the Spamhaus DDoS attack in March.”
Not long after McDonough’s arrest, a new Facebook page went online called “Freenarko,” which listed itself as “a solidarity support group to help in the legal defense and media stability for ‘Narko,’ a 16-yr old brother in London who faces charges concerning the Spamhaus DDoS attack in March.”
Multiple posts on that page link to Stophaus propaganda, to the Facebook page for the Church of the Common Good, and to a now-defunct Web site called “WeAreHomogeneous.org” (an eye-opening and archived copy of the site as it existed in early 2013 is available at archive.org; for better or worse, the group’s Facebook page lives on).
The Church of Common Good lists as its leader a Gulfport, Fla. man named Andrew J. Stephens, whose LinkedIn page says he is a “media mercenary” at the same organization (hours after this story was posted, large chunks of text were deleted from Stephens’ profile; a PDF of the original profile is here).
Stephens’ CV lists a stint in 2012 as owner of an email marketing firm variously called Digital Dollars and IBT Inc, moneymaking schemes which Stephens describes as a “beginner to intermediate level guide to successful list marketing in today’s email environment. It incorporates the use of both white hat and some sketchy techniques you would find on black hat forums, but has avoided anything illegal or unethical…which you would also find on black hat forums.”
More recent entries in Andrew’s LinkedIn profile show that he now sees his current job as a “social engineer.” From his page:
“I am a what you may call a “Social Engineer” and have done work for several information security teams. My most recent operation was with a research team doing propaganda analysis for a media firm. I have a unique ability to access data that is typically inaccessible through social engineering and use this ability to gather data for research purposes. I have a knack for data mining and analysis, but was not formally trained so am able to think outside the box and accomplish goals traditional infosec students could not. I am proficient at strategic planning and vulnerability analysis and am often busy dissecting malware and tracking the criminals behind such software. There’s no real title for what I do, but I do it well I am told.”
Turns out, Andrew J. Stephens used to have his own Web site — andrewstephens.org. Here, the indispensable archive.org helps out again with a cache of his site from back when it launched in 2011 (oddly enough, the same year that Stophaus claims to have been born). On his page, Mr. Stephens lists himself as an “internet entrepreneur” and his business as “IBT.” Under his “Featured Work” heading, he lists “The Stophaus Project,” “Blackhat Learning Center,” and a link to an spamming software tool called “Quick Send v.1.0.”
Stephens did not return requests for comment sent to his various contact addresses, although a combative individual who uses the Twitter handle @Stophaus and has been promoting the group’s campaign refused to answer direct questions about whether he was in fact Andrew J. Stephens.
Helpfully, the cached version of Andrewstephens.org lists a contact email address at the top of the page: stephensboy@gmail.com (“Stephensboy” is the short/informal name of the Andrew J. Stephens LinkedIn profile). A historic domain registration record lookup purchased from Domaintools.com shows that same email address was used to register more than two dozen domains, including stophaus.org and stopthehaus.org. Other domains and businesses registered by that email include (hyperlinked domains below link to archive.org versions of the site):
-“blackhatwebhost.com“;
-“bphostingservers.com” (“BP” is a common abbreviation for “bulletproof hosting” services sold to -spammers and malware purveyors);
-“conveyemail.com”;
-“datapacketz.com” (another spam software product produced and marketed by Stephens);
-“emailbulksend.com”;
-“emailbulk.info”;
-“escrubber.info” (tools to scrub spam email lists of dummy or decoy addresses used by anti-spam companies);
-“esender.biz”;
-“ensender.us”;
-“quicksendemail.com“;
-“transmitemail.com”.
The physical address on many of the original registration records for the site names listed above show an address for one Michelle Kellison. The incorporation records for the Church of Common Good filed with the Florida Secretary of State list a Michelle Kellison as the registered agent for that organization.
Putting spammers and other bottom feeders in jail for DDoS attacks may be cathartic, but it certainly doesn’t solve the underlying problem: That the raw materials needed to launch attacks the size of the ones that hit SpamHaus and CloudFlare last year are plentiful and freely available online. As I noted in the penultimate chapter of my new book — Spam Nation (now a New York Times bestseller, thank you dear readers!), the bad news is that little has changed since these ultra-powerful attacks first surfaced more than a decade ago.
Rodney Joffe, senior vice president and senior technologist at Neustar –a security company that also helps clients weather huge online attacks — estimates that there are approximately 25 million misconfigured or antiquated home and business routers that can be abused in these digital sieges. From the book:
Most of these are home routers supplied by ISPs or misconfigured business routers, but a great many of the devices are at ISPs in developing countries or at Internet providers that see no economic upside to spending money for the greater good of the Internet.
“In almost all cases, it’s an option that’s configurable by the ISP, but you have to get the ISP to do it,” Joffe said. “Many of these ISPs are on very thin margins and have no interest in going through the process of protecting their end users— or the rest of the Internet’s users, for that matter.”
And therein lies the problem. Not long ago, if a spammer or hacker wanted to launch a massive Internet attack, he had to assemble a huge botnet that included legions of hacked PCs. These days, such an attacker need not build such a huge bot army. Armed with just a few hundred bot- infected PCs, Joffe said, attackers today can take down nearly any target on the Internet, thanks to the millions of misconfigured Internet routers that are ready to be conscripted into the attack at a moment’s notice.
“If the bad guys launch an attack, they might start off by abusing 20,000 of these misconfigured servers, and if the target is still up and online, they’ll increase it to 50,000,” Joffe said. “In most cases, they only need to go to 100,000 to take the bigger sites offline, but there are 25 million of these available.”
If you run a network of any appreciable size, have a look for your Internet addresses in the Open Resolver Project, which includes a searchable index of some 32 million poorly configured or outdated device addresses that can be abused to launch these very damaging large-scale attacks.