I thought this Christmas I would recount with you some of my experiences over the last four years to help bolster debate on what is an appropriate role for government in the Internet copyright policy debate between Hollywood and Internet technologies.
I thought this Christmas I would recount with you some of my experiences over the last four years to help bolster debate on what is an appropriate role for government in the Internet copyright policy debate between Hollywood and Internet technologies.
I continue to have hope that the New Year will bring freedom for my colleagues and me, hope to millions of others striving for fair and predictable rules governing the Internet, and wisdom to political leaders for making good decisions on whether and how armed police forces and government spies should be utilized in Internet copyright matters.
1. Raid and Seizure of Nearly Everything
It has been almost four years since helicopters and paramilitary police officers descended on my peaceful mansion in Coatesville, New Zealand.
As a personal birthday gift from the United States government, armed with automatic weapons, side harms, bullet-proof vests and attack dogs, they pulled my pregnant wife, infant children, staff and friends out into the cold morning air to make a Hollywood spectacle of an arrest that could have been executed with a simple knock on my door.
So began my first-hand education in the high-stakes game of international copyright law, extradition treaties, global politics and the power Hollywood wields through the U.S. government.
Just after the raid my attorney, Ira Rothken, aptly stated that the government was acting like a “copyright extremist” by taking down one of the world’s largest cloud storage services “without any notice or chance for Megaupload to be heard in a court of law.” The result is both “offensive to the rights of Megaupload but also to the rights of millions of consumers worldwide” who stored personal data with the service.
That same day, the U.S. government enlisted authorities in Hong Kong, Germany, New Zealand, the Philippines, Canada and the Netherlands to seize every asset imaginable, from bank accounts to computer servers, from cars to mobile phones. I, of course, watched from a jail cell – guilty until proven innocent. It would take about a month and a ton of legal wrangling before the court released me on bail.
2. Dubious Legal Theories/Lessig
Over the course of these years, I have learned with ever greater conviction what I knew in my gut just had to be true – Megaupload and my colleagues and I should not be prosecuted for criminal copyright infringement operating a cloud storage site.
The powerful opinion from Harvard Law Professor Lawrence Lessig, a leading if not the leading Internet Copyright authority in the U.S. (and the World), completely dismantled the core of the United States case. Professor Lessig revealed the complete lack of a criminal statute for secondary copyright infringement. He summarized his thirty-seven page dissection (pdf) of the United States case at the start:
“It is my opinion that the Superseding Indictment and Record of the Case filed by the United States Department of Justice (‘DOJ’) do not meet the requirements necessary to support a prima facie case that would be recognized by United States federal law and subject to the extradition treaties between New Zealand and the United States. On the whole, the filings are not reliable.”
The fallacy of the case against us was clearly articulated to the world. I felt a sense of validation of my integrity, while at the same time the pain of the grim reality taught by the preceding years, that right does not necessarily beat might.
Assuming the Government disagrees with Professor Lessig how can a non lawyer like me be held criminally liable or have what is known as criminal mens rea when even leading legal scholars disagree on what the criminal law is in a case of first impression? Professor Lessig knows that pain, living the memory of his friend Aaron Swartz, and I am forever grateful for his providing his opinion for no compensation, no doubt at least in part in his honor.
3. Complete Shutdown of Megaupload/Consumer Access
One of the most painful and angering aspects of this whole prosecution, arrest and seizure is not their impact on me, which has been devastating, but on the wholesale shutdown of Megupload globally, the loss of hundreds of jobs, and the severing of consumers and businesses from their own data, rightfully stored on Megaupload and lawfully shared with friends, family, colleagues and collaborators. Just two examples are those of, Michael Weinberg, a staff attorney at the rights watchdog Public Knowledge, who remarked:
“As luck would have it, over the weekend I used my home laptop to pull down the stream of the House Judiciary Committee [Stop Online Piracy Act] markup. I wanted to transfer it here to work so that I could cut it up into a video we were using. I uploaded it, but before I had a chance to download it Megaupload was shut down. I can’t speak for everything happening on the site, but Megaupload was providing me a completely legitimate service for a completely legitimate end.”
And Kyle Goodwin, who has fought, with the aid of the Electronic Frontier Foundation, to get the U.S. government to let him have his data. Mr. Goodwin used Megaupload to run a business making children’s sports videos for parents. His counsel articulated the U.S. government’s disregard for the rights of legitimate users:
“In no area of commercial or personal activity is the government allowed to seize property without taking reasonable measures to avoid unnecessary harm and loss of commercial value. That should be no less true when the property is information.
“Thus, if the government is going to get into the business of seizing Internet properties used to host a wide range of content — infringing and not — it must implement procedures and standards for protecting the property and due process rights of innocents such as Mr. Goodwin who use those services for legitimate purposes. Since the government seems uninterested in developing those processes and standards itself, this case should serve as a starting point for the judiciary to do so.”
4. Misleading basis for Shutdown (39 Files etc.)
One of the most upsetting abuses we learned was how the U.S. prosecution team mischaracterized facts and omitted exculpatory evidence from its applications for warrants to seize Megaupload’s domain names. My legal team outlined this in their Federal Court submissions.
In summary Megaupload was cooperating with a U.S. government investigation and search warrant into alleged infringement by a third-party user of the service. Megaupload at the request of the DOJ left intact certain files identified to it by the government, in order to preserve the status quo and the integrity of the FBI’s investigation. Subsequently, in its applications to seize the company’s domain names, the government would tell the federal court that the company had been told about those infringing files or movies, but had failed to take them down, omitting the fact that Megaupload did so in order to cooperate with the ongoing government request and investigation.
The prosecution’s selective omission flipped the import of the facts on their head, turning government cooperation into erroneous criminal intent. Moreover, the government’s twisted characterization was the core direct evidence of intent it offered to the court in support of its applications. According to my lawyer’s submissions had the exculpatory evidence been included in the applications, it seems likely that the warrants could not have issued.
It is difficult to imagine a more abusive tactic. The domain orders were requested from a federal magistrate judge on an ex parte basis; no one was in court to correct the prosecution’s story or to explain why the seizure orders should not be issued. If the U.S. government decided to act properly, to be forthright, not to omit key facts selectively to suit its purpose, the warrant may not have been issued and Megaupload would still be in business. Now it is too late; the company became extinct the moment its domain names were seized. The question keeps coming to mind, who are the real, “pirates”?
5. Destruction of Data
I find it astonishing that the U.S. government was able to seize all our data and funds and kill our company, then take no responsibility for preserving the data belonging to innocent users and important evidence for prosecuting and defending a criminal copyright case.
The Megaupload servers in Virginia alone contained about 25 petabytes of data, yet the government allowed those to be taken offline for lack of funding. Moreover, the U.S. government initially was content to let the data on the servers be destroyed, and although that has not occurred, the equipment has been gathering dust for many years and is in danger of deteriorating.
As I write this it seems likely that the DOJ permitted the destruction data on the Megaupload servers in the Netherlands. The U.S. government will not agree to release a single penny of Megaupload funds to allow for consumers to get access to their data, or to preserve the evidence, or even to mount a legal defense in the United States.
6. Illegal Spying
While it is now public knowledge, when we discovered the truth we were stunned that a New Zealand government intelligence arm was persuaded to illegally spy on me. Those due process abuses were eventually brought to light in court proceedings, forcing New Zealand’s Prime Minister to issue a public apology.
Even though they admitted the facts of their misconduct, the damage was done not only to me but to the integrity of our democracy as a whole.
7. Illegally removing data from NZ
Several years ago, the New Zealand court determined that the U.S. government had transferred hard drive data belonging to my colleagues and me out of New Zealand in violation of New Zealand law.
Years later, the U.S. authorities have refused to return the data, despite the fact that they were acquired illegally and in violation of my privacy rights, and notwithstanding their importance to any defense against the criminal charges. The United States has availed themselves of the New Zealand courts to try to extradite me but they refuse to follow that same court’s orders.
8. Interference on access to own evidence
One further frustrating aspect of trying to put together a complete defense over the past four years has been the New Zealand government’s refusal to return our own computers and data that were seized on the day of the raid. 1000 days later and not until the virtual eve of the extradition hearing, that began in late September, 2015, were materials reluctantly returned. Having succeeded in their effort to make us fight with our hands behind our backs, the government acted as though there was no harm done.
9. Starve out strategy while presumed innocent/Blocking Payment to US Experts and Lawyers
I have learned at least one good lesson. I learned that the judicial system of a small nation such as New Zealand can stand tall for the rights of the accused and give real meaning to the term “innocent until proven guilty.” While the extradition process has been in motion, I have at least been allowed access to my money to live and defend myself by the New Zealand courts.
But again the United States refused to honor or give comity to the New Zealand court orders resulting in our inability to use such unfrozen funds to pay anyone who is a US citizen such as US lawyers and expert witnesses to assist at the extradition hearing. I was fortunate to have my US lawyer Ira Rothken generously assist and work with Professor Lessig for no payment but we were unable to retain numerous technical and other experts to testify.
10. Fugitive Disentitlement while lawfully opposing extradition
The U.S. DOJ doubled-down on its starve-out strategy in 2014 with the filing of a civil forfeiture action against the seized assets and the application of the “fugitive disentitlement doctrine.”
Civil forfeiture allows the U.S. DOJ to go after assets it alleges are the proceeds of a crime. Claimants are able to file claims and oppose the action – that is, UNLESS they are “FUGITIVES.” Despite never residing in or even visiting the United States, the U.S. DOJ asserted and the U.S. District Court agreed that I was a fugitive, because I could voluntarily surrender to the United States, travel in chains and be locked in a cell pending a trial in Alexandria, Virginia.
Since I was unwilling to do so without an agreement on living conditions and access to funds, which the U.S. DOJ would not hear of, I was not allowed to oppose the civil forfeiture and, by default judgment, the U.S. District Court ordered all our previously seized assets to be completely forfeited to the United States.
Fortunately, even though the United States opposed release of my funds held in New Zealand and Hong Kong, the courts in those countries demonstrated a greater respect to natural justice.
Orders by the courts in both those countries have released restrained or so called “forfeited” funds for living and legal expenses, enabling me to at least pay for my New Zealand counsel.
The U.S. strategy was not without impact, though, as in the eyes of the United States, all our forfeited assets now belong to the United States. While funds have been released by New Zealand and Hong Kong to challenge extradition, I am not able to use those funds for anyone but New Zealand counsel. This has deprived me of critical tools (including evidence stored on servers, payments to US counsel, and payments to legal, technical and industry expert witnesses) to defend an extradition proceeding of this magnitude and complexity.
I hope the U.S. 4th Circuit Court of Appeals will reverse the “fugitive disentitlement” ruling, we will prevail in the civil forfeiture case and we will have access to our funds. Otherwise, if we are extradited, I will be penniless upon arrival in the United States.
If the criminal prosecution goes to trial, defending it will be at an extraordinary cost. A huge amount will be needed for e-discovery, likely in the millions of dollars. Further legal and expert fees will be at a level far beyond expenditure to date in New Zealand, which has been in the tens of millions.
With no funds, I would be left reliant on the Public Defender. That office is in no position or expertise to defend a copyright case of this magnitude – the “largest criminal copyright case in history.”
11. Duty of Candor Violations/92B/Erroneous Use of Simple Fraud Theory
As I understand it, the U.S. government is supposed to present its extradition requests to New Zealand with a “Duty of Candor.” Looking back on how the initial seizure warrants were obtained, one might doubt that “Candor” was a high priority.
Not surprisingly, close scrutiny of basic evidence in the Record of the Case (“ROC”) revealed a failure of that duty. For example, evidence was misrepresented and simple quotations of emails and Skype message were cherry-picked, taken out of context or even improperly translated to paint an intended adversarial picture, rather than present candid facts. US translations of German communications are demonstrably inaccurate and self-serving.
For example, the US mistranslates a quote to imply something more sinister than actually stated. The US translation of a phrase is presented as, “at some point a judge will be convinced about how evil we are and then we’re in trouble.” Three independent translators, however, have translated the phrase as, “Because at some stage a judge will be talked into how bad we allegedly are and then it will be a mess.”
In another quote, the US translation, “since the special people uploaded and promoted more” implies a sinister scheme with others, when, in fact, the independent translation was merely that, “People have uploaded and promoted more since the special.”
For all such translations, the US has not made available the original text. Moreover, the US has not made available surrounding context which informs tenor of communications relied upon, including both German translations and English communications.
The legal arguments presented by our legal team reveal the failure of the duty of candor. A particularly interesting one is that fact the New Zealand Copyright Act contains a section 92B, which creates a safe harbor for a cloud storage ISP from criminal copyright liability arising out of user site usage. The statute overtly provides for a criminal safe harbor.
From a logic perspective my lawyer’s submissions argued that we shouldn’t have to even disprove criminal liability to avail ourselves of the criminal safe harbor otherwise the safe harbor would be rendered meaningless.
Not to be blindsided and ever creative, the U.S., ably represented by New Zealand’s Crown Law, came up with a new twist – instead of seeking extradition for copyright infringement, they decided to call it “fraud.” Nevermind that the U.S. indictment did not allege fraud (for good reason, since according to our submissions US case law clearly said that copyright preempts fraud).
This argument by the U.S. ultimately revealed that the prosecution would go to any lengths, create any argument, misstate any fact, to win their case. Justice and fairness been tossed out long ago, at least before the start of 2012.
12. It’s political
If you have read all of the above you may wonder why the US Government is acting so badly. This case is a political thriller authored and produced by the MPAA and its Senator for hire Chris Dodd. His lobbying, calling in favors and close relationships within the White House made this unprecedented abuse of power possible. If you are intrigued to learn more you may want to read my whitepaper (pdf)
Now, the next phase of this saga is in the hands of New Zealand District Judge Dawson. Having patiently listened to submissions and testimony for two months, he must wade through the sea of novel arguments to determine if I and my fellow Megaupload associates should be extradited to the United States to fight the first of its kind criminal prosecution for secondary copyright infringement.
Merry Christmas and a Happy New Year to all of you.
Kim Dotcom
Update: On Wednesday, Judge Dawson determined that Kim Dotcom and his former Megaupload associates are eligible for extradition to the United States.
Source: TorrentFreak, for the latest info on copyright, file-sharing, torrent sites and ANONYMOUS VPN services.

 Call me old-fashioned or just plain old, but when people blatantly break the law in a public place I find that somewhat bemusing – especially if there is absolutely no gain in doing so.
Call me old-fashioned or just plain old, but when people blatantly break the law in a public place I find that somewhat bemusing – especially if there is absolutely no gain in doing so.
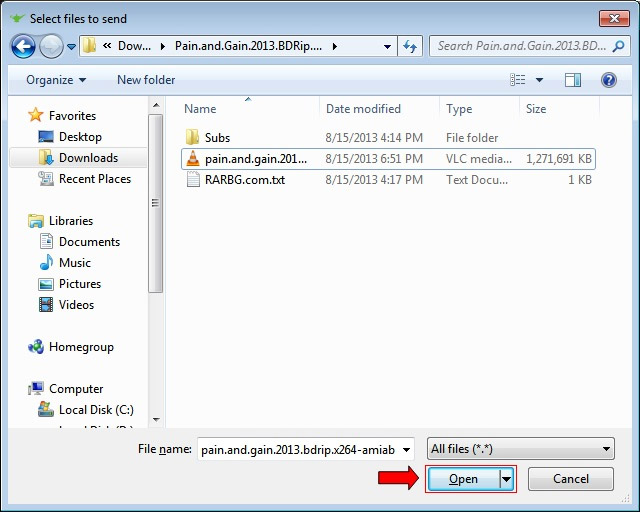
 Late last week millions of pirates cheered behind their computers as the “screener season” finally got underway.
Late last week millions of pirates cheered behind their computers as the “screener season” finally got underway. 
 I thought this Christmas I would recount with you some of my experiences over the last four years to help bolster debate on what is an appropriate role for government in the Internet copyright policy debate between Hollywood and Internet technologies.
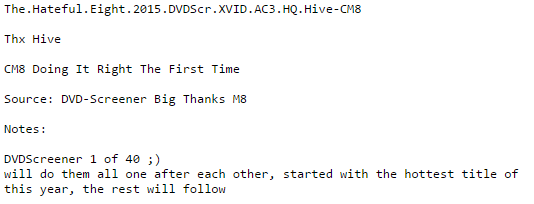
I thought this Christmas I would recount with you some of my experiences over the last four years to help bolster debate on what is an appropriate role for government in the Internet copyright policy debate between Hollywood and Internet technologies. Last weekend several high quality screener copies started to
Last weekend several high quality screener copies started to 
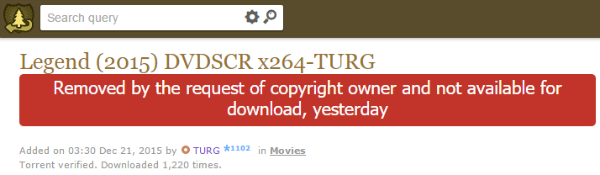
 With the majority of all commercially available software slushing round on the Internet in pirate form, companies have always sought secure anti-piracy mechanisms to protect their products.
With the majority of all commercially available software slushing round on the Internet in pirate form, companies have always sought secure anti-piracy mechanisms to protect their products.