New Foxtel Blocking Application Targets Streaming, Torrent & Proxy Sites
lundi 1 juillet 2019 à 10:50
Following the introduction of amendments to copyright law in 2018, it is now easier than ever to have ‘pirate’ sites blocked by ISPs in Australia.
The new rules mean that regular ‘pirate’ sites such as streaming and torrent platforms, as well as any service that has the primary purpose and/or primary effect of facilitating access to infringing content, can be targeted.
On June 18, 2019, Foxtel returned to the Federal Court in Sydney with a new blocking application. The court has yet to make the associated documents public but TorrentFreak was able to obtain them via a third-party source.
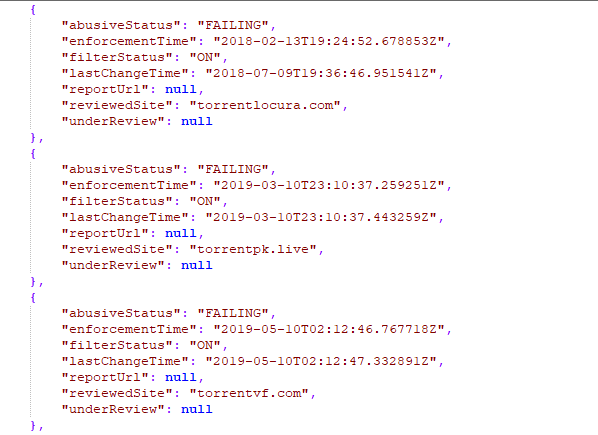
They reveal Foxtel writing to ISPs – TPG, Telstra, Optus, Vocus, Vodafone, plus their subsidiaries (52 in total) – at the end of May, indicating its intention to file an application to have a total of 35 torrent, streaming and proxy site domains blocked via court order.
Streaming ‘Target Online Locations’
The sites in this category are described as providing Internet users “with a browsable and/or searchable index or directory of digital (including audiovisual) content from which they can select content of their choice”.
Transmission of this content from the sites either takes place directly or through a “frame” which presents the content from another location. Or, alternatively, the sites provide lists of hyperlinks that allow users to access content after being redirected to another platform.
The sites targeted are ShareMovies, SeriesOnline8, Movie4U, SeeHD, StreamDreams and MoviesOnline.
Torrent ‘Target Online Locations’
Sites under this heading are described as having a browsable or searchable index of digital content or facilitating access to the same on other ‘online locations’. They provide users with access to .torrent files (or links to the same) which provide access to content without charge.
The sites targeted are WatchSoMuch, TorrentKen and SkyTorrents.
Proxy “Target Online Locations”
Given the changes to the law last year, proxy sites – which often exist to enable access to sites that are blocked by court order – can now be subject to blocking requests since they have the “primary effect” of facilitating access to infringing content.
The sites in the Foxtel application are described as providing Internet users with a browsable/searchable index of proxies providing access to streaming and torrent sites, including those sites listed above.
“[E]ach of the Proxy TOLs provides, or facilitates, free access for Internet users to content which it is not licensed to provide” the application reads, adding that none have “legitimate functions”.
The sites targeted are Unblocked.lol, Unblocked.win, Unblockall, Unblocker, and MyUnblock.
A case management hearing is booked for July 11, 2019.
The full list of URLs requested for blocking is as follows: sharemovies.net, seriesonline8.co, seriesonline8.com, movie4u.live, movie4u.cc, movie4u.co, seehd.uno, seehd.biz, streamdreams.org, streamdreams.me, streamdreams.co, streamdreams.online, streamdreams.video, stream-dreams.com, moviesonline.mx, wsmmirror.info, watchsomuch.info, watchsomuch.com, seventorrentsmirror.info, seventorrentsproxy.com, 7tmirror.info, torrentken.site, skytorrents.lol, unblocked.lol, unblocked.is, unblocked.ms, unblocked.win, unblocked.gdn, unblocked.vet, unblocked,sh, unblocked.mx, unblockall.org, unblocker.cc, unblock.win, myunblock.com
Source: TF, for the latest info on copyright, file-sharing, torrent sites and more. We also have VPN reviews, discounts, offers and coupons.
 Video streaming is more popular than ever. This is true for the YouTubes and Netflixes of this world, but also for pirate sites.
Video streaming is more popular than ever. This is true for the YouTubes and Netflixes of this world, but also for pirate sites.

 Online advertising can be quite a nuisance. Flashy and noisy banners, or intrusive pop-ups, are a thorn in the side of many Internet users.
Online advertising can be quite a nuisance. Flashy and noisy banners, or intrusive pop-ups, are a thorn in the side of many Internet users.