Researcher Finds Critical Vulnerabilities in Hollywood Screener System
vendredi 9 septembre 2016 à 17:26 So-called screener copies of the latest movies are some of Hollywood’s most valuable assets, yet every year and to the delight of pirates, many leak out onto the Internet.
So-called screener copies of the latest movies are some of Hollywood’s most valuable assets, yet every year and to the delight of pirates, many leak out onto the Internet.
Over the years, Hollywood has done its best to limit the leaks, but every 12 months without fail, many of the top titles appear online in close to perfect quality.
With that in mind, the studios have been testing Netflix-like systems that negate the need for physical discs to be sent out.
One such system has been made available at Awards-Screeners.com. Quietly referenced by companies including 20th Century Fox, the site allows SAG-AFTRA members and other industry insiders to view the latest movies in a secure environment. At least, that’s the idea.

Late August, TorrentFreak was contacted by security researcher Chris Vickery of MacKeeper.com who told us that while conducting tests, he’d discovered an exposed MongoDB database that appeared to be an integral part of Awards-Screeners.com.
“The database was running with no authentication required for access. No username. No password. Just entirely exposed to the open internet,” Vickery told TF.
The researcher’s discovery was significant as the database contained more than 1,200 user logins. Vickery did not share the full database with TF but he did provide details of a handful of the accounts it contained. Embarrassingly, many belong to senior executives including:
– Vice President of International Technology at Universal Pictures
– Director of Content Technology & Security at Disney
– Vice President of Post-Production Technology at Disney
– Executive Director, Feature Mastering at Warner Bros
– Vice President of Global Business & Technology Strategy at Warner Bros
– Director of Content Protection at Paramount Pictures
– VP of corporate communications and publicity for 20th Century Fox
While the hashed passwords for the above would be difficult to crack, the database itself was publicly offering admin-level access, so it was a disaster from a security perspective.
“Any of the values in the database could have been changed to arbitrary values, i.e. create-your-own-password,” Vickery said.

According to the researcher, this vulnerability had the potential to blow a hole in the screener system and could’ve had huge piracy and subsequent law enforcement implications.
“Theoretically, it would have been possible for a malicious person to log into any of the 1,200+ user accounts, screencap an unreleased film, and torrent it to the world,” he explained.
“There’s also supposedly video watermark technology that makes it possible to trace which account it came from. So basically you could have framed any of the users for the distribution as well by using their account to do it.”
The screenshot below shows Vickery’s view of the database, in this case highlighting the availability of a screener copy of the soon-to-be-released Oliver Stone movie, Snowden.
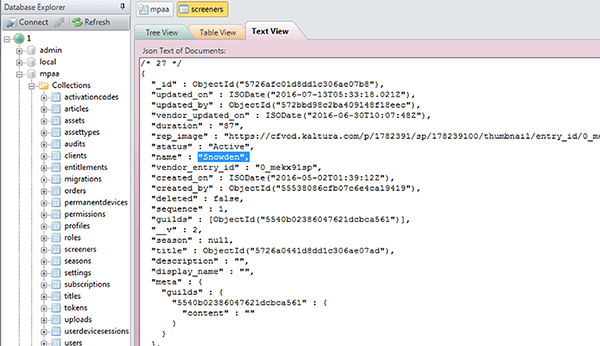
Vision Media Management, which claims to be the largest Awards screener fulfillment operation in the world, is the outfit in charge of the system. It’s described in the company’s promotional material as a “Secure Digital Screener” platform “selected by the MPAA major studios as the preferred secure content delivery method for Awards voters.”
Like all responsible data breach hunters, Vickery did his research and decided to inform Awards-Screeners.com and Vision Media Management of his findings. Initially, they appeared somewhat grateful.
“During my telephone conversation with Vision Media Management, which consisted of me, their lead counsel (Tanya Forsheit), and their CTO (Doug Woodard), they were very surprised and worried. They didn’t understand how this could happen and claimed that the system should have nothing loaded into it currently and was purged months ago,” Vickery said.
“This is not believable due to time stamps of activity in the database. In the ‘Snowden’ screenshot, for example, you can see that the entry was updated on 7/13/2016.”

Vickery also informed the MPAA of his discoveries and was told by the organization’s Office of Technology that it was “currently working diligently” with Vision to “evaluate the situation and take appropriate remedial action.”
Meanwhile, conversations between Vickery and Vision Media Management continued. The researcher says that the company tried to downplay his findings with claims that the database had been secure and contained only test data.
 However, when Vickery asked if he could release the database, he was advised it was too sensitive to be made public. The company then began a drive to convince the researcher that security at Amazon, one of Vision’s vendors, was to blame for the leak. Vision’s lawyer also suggested that Vickery had “improperly downloaded” the database.
However, when Vickery asked if he could release the database, he was advised it was too sensitive to be made public. The company then began a drive to convince the researcher that security at Amazon, one of Vision’s vendors, was to blame for the leak. Vision’s lawyer also suggested that Vickery had “improperly downloaded” the database.
In a follow-up mail, Vickery made it clear to Vision that allegations of “improper downloading” were incompatible with the fact that the database had been published openly to the public Internet. And, after all, he had done the responsible thing by informing them of their security issues.
“I have cooperated with and contributed to data breach-related investigations conducted by the FTC, FBI, US Navy, HHS/OCR, US Secret Service, and other similar entities,” he told the company. “Not a single regulatory or government agency I have interacted with has even suggested that what I do, downloading publicly published information, is improper.”
In subsequent discussion with Vickery, Vision Media asked for time to assess the situation but by September 4, the researcher had more bad news for the company.
Emails shared with TF show Vickery informing Vision of yet more security holes in its system, specifically a pair of publicly exposed S3 buckets located on Vision resources at Amazon. Vickery says these contained development and release builds of Vision’s Android app, development and deployment meeting notes, plus some unexplained references to Netflix.
In the run-up to this piece, Vickery advised Vision Media that a public disclosure would be likely so in an effort to provide balanced reporting, TorrentFreak reached out to Vision Media’s CEO for a statement on the researcher’s findings. At the time of publication, nothing had been received.
And after several conversations with Vision via email and on the phone, Vickery was drawing a blank this week too.
“Vision has not gotten back to me today, and we were very clear last week that they would be contacting me again by Thursday,” Vickery told TF. “I even sent them a little reminder earlier and asked if we were still planning to talk. No response all day.”
In the absence of an official statement from Vision Media, it’s impossible to say how many people accessed the Awards-Screener database before Vickery, or what their intentions were. Perhaps only time will tell but one thing is clear – a move to the digital space might not be the perfect solution for screener distribution.
Check out Chris Vickery’s report on MacKeeper
Source: TF, for the latest info on copyright, file-sharing, torrent sites and ANONYMOUS VPN services.
 With more than 150 million users a month, uTorrent is by far the most popular torrent client in the West.
With more than 150 million users a month, uTorrent is by far the most popular torrent client in the West.

 In recent years file-sharers around the world have been threatened with lawsuits, if they don’t pay a significant settlement fee.
In recent years file-sharers around the world have been threatened with lawsuits, if they don’t pay a significant settlement fee.
 Last December a New Zealand District Court ruled that Kim Dotcom and his colleagues can be sent to the United States to face criminal charges.
Last December a New Zealand District Court ruled that Kim Dotcom and his colleagues can be sent to the United States to face criminal charges. 
