‘Revolution’ Crimeware & EMV Replay Attacks
mercredi 1 avril 2015 à 22:14In October 2014, KrebsOnSecurity examined a novel “replay” attack that sought to exploit implementation weaknesses at U.S. financial institutions that were in the process of transitioning to more secure chip-based credit and debit cards. Today’s post looks at one service offered in the cybercrime underground to help thieves perpetrate this type of fraud.
Several U.S. financial institutions last year reported receiving tens of thousands of dollars in fraudulent credit and debit card transactions coming from Brazil and hitting card accounts stolen in recent retail heists, principally cards compromised as part of the October 2014 breach at Home Depot. The affected banks were puzzled by the attacks because the fraudulent transactions were all submitted through Visa and MasterCard‘s networks as chip-enabled transactions, even though the banks that issued the cards in question hadn’t yet begun sending customers chip-enabled cards.
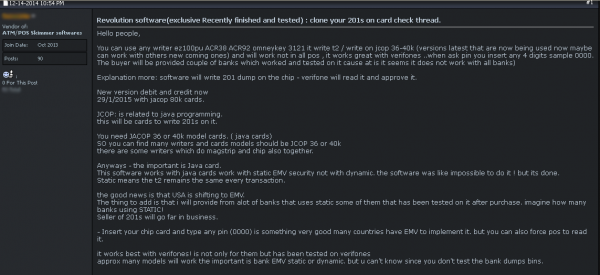
Seller in underground forum describes his “Revolution” software to conduct EMV card fraud against banks that haven’t implemented EMV fully.
Fraud experts said the most likely explanation for the activity was that crooks were pushing regular magnetic stripe transactions through the card network as chip card purchases using a technique known as a “replay” attack. According to one bank interviewed at the time, MasterCard officials explained that the thieves were likely in control of a payment terminal and had the ability to manipulate data fields for transactions put through that terminal. After capturing traffic from a real chip-based chip card transaction, the thieves could insert stolen card data into the transaction stream, while modifying the merchant and acquirer bank account data on-the-fly.
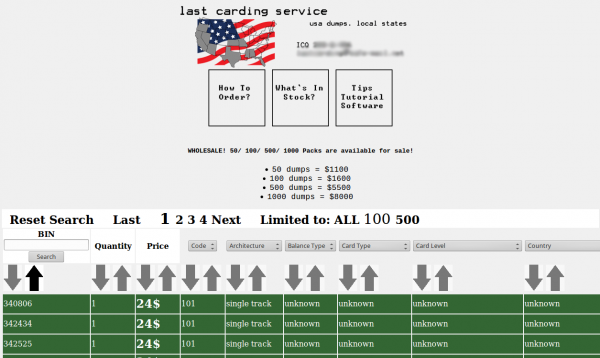
Recently, KrebsOnSecurity encountered a fraudster in a popular cybercrime forum selling a fairly sophisticated software-as-a-service package to do just that. The seller, a hacker who reportedly specializes in selling skimming products to help thieves steal card data from ATMs and point-of-sale devices, calls his product “Revolution” and offers to provide buyers with a list of U.S. financial institutions that have not fully or properly implemented systems for accepting and validating chip-card transactions.
First, a bit of background on chip-based cards is in order. Chip cards are synonymous with a standard called EMV (short for Europay, MasterCard and Visa), a global payment system that has already been adopted by every other G20 nation as a more secure alternative to cards that simply store account holder data on a card’s magnetic stripe. EMV cards contain a secure microchip that is designed to make the cards very difficult and expensive to counterfeit.
There are several checks that banks can use to validate the authenticity of chip card transactions. The chip stores encrypted data about the cardholder account, as well as a “cryptogram” that allows banks to tell whether a card or transaction has been modified in any way. The chip also includes an internal “counter” mechanism that gets incremented with each sequential transaction, so that a duplicate counter value or one that skips ahead may indicate data copying or other fraud to the bank that issued the card.
It appears that the Evolution software is designed to target banks that are in the process of architecting their payment networks to handle EMV transactions, but that nevertheless aren’t yet properly checking the EMV cryptogram and/or counter for these transactions. It also seems that some banks have inexplicably lowered their fraud controls on EMV transactions, even though they are not yet taking advantage of the added security protections offered by chip-based cards.
“The reason I think they bother to fake EMV transactions is that they know the EMV card issuing banks relax their fraud controls on them and don’t have it implemented properly and therefore they do not properly check the dynamic EMV data,” said Avivah Litan, a fraud analyst with Gartner Inc.
That’s precisely what the fraudster selling Evolution points out in his somewhat awkwardly-worded sales thread for his product, which he said relies on Java card software capable of writing to chip and mag-stripe based cards. Java Card refers to a software technology that allows Java-based applications (applets) to be run securely on smart cards and similar small memory footprint devices. Java Card is the tiniest of Java platforms targeted for embedded devices, and was originally developed for the purpose of securing sensitive information stored on smart cards.
“The good news is that USA is shifting to EMV,” he writes. “ This software works with Java cards work with static EMV security not with dynamic. Static means the [counter] remains the same every transaction. The thing to add is that I will provide from a lot of banks that uses static some of them that has been tested on it after purchase. Imagine how many banks using STATIC!“
This same fraudster appears to be the operator of an online store called “Last Carding,” which sells stolen credit cards and includes a number of tutorials on how to conduct card fraud. The crook running this site says he’s online twice a day, but that he takes Sundays off. Interestingly, the clock on his Web store says he operates on Central America time (-06:00 GMT).