Hacked Hotel Phones Fueled Bank Phishing Scams
mercredi 4 février 2015 à 22:05A recent phishing campaign targeting customers of several major U.S. banks was powered by text messages directing recipients to call hacked phone lines at Holiday Inn locations in the south. Such attacks are not new, but this one is a timely reminder that phishers increasingly are using lures blasted out via SMS as more banks turn to text messaging to communicate with customers about account activity.
 The above-mentioned phishing attacks were actually a mix of scams known as “SMiShing” — phishing lures sent via SMS text message — and voice phishing or “vishing,” where consumers are directed to call a number that answers with a voice prompt spoofing the bank and instructing the caller to enter his credit card number and expiration date.
The above-mentioned phishing attacks were actually a mix of scams known as “SMiShing” — phishing lures sent via SMS text message — and voice phishing or “vishing,” where consumers are directed to call a number that answers with a voice prompt spoofing the bank and instructing the caller to enter his credit card number and expiration date.
Over the past two weeks, fraudsters have been blasting out SMS messages to hundreds of thousands of mobile users in the Houston, Texas area. The messages alerted recipients about supposed problems with their bank account, urging them to call a supplied number and follow the automated voice prompts to validate or verify their credit card account information.
On Saturday, Jan. 30, I called one of the numbers that was sent out in the smishing/vishing scam — 281-866-0500 – which is the main phone line for a Holiday Inn Express in Houston. At the time, calls to the number went straight to an automated voice prompt targeting Bank of America customers:
“Thank you for calling Bank of America. A text message has been sent to inform you that your debit card has been limited due to a security issue. To reactivate, please press one now.” After pressing one, the caller is prompted to enter the last four digits of their Social Security number, and then the full card number and expiration date.
My recording of the call was garbled, but here’s a copy of a very similar voice prompt targeting Key Bank customers earlier in January that also was run off the fax line tied to a different Holiday Inn a few miles away in Houston [number: 832-237-8999], according to Numbercop, a telephony threat intelligence firm.
Holiday Inn’s corporate office did not return calls seeking comment, but the company apparently got the message because the phone lines were answering normally on Monday. A front desk clerk who answered the line on Tuesday said the hotel received over 100 complaints from people who got text messages prompting them to call the hotel’s main number during the time it was hacked.
According to Jan Volzke, Numbercop’s chief executive, these scams typically start on a Saturday afternoon and run through the weekend when targeted banks are typically closed.
“Two separate Holiday Inns getting hijacked in such short time suggests there is a larger issue at work with their telephone system provider,” he said. “That phone line is probably sitting right next to the credit card machine of the Holiday Inn. In a way this is just another retail terminal, and if they can’t secure their phone lines, maybe you shouldn’t be giving them your credit card.”
Volzke said the recipients of the phony texts in Houston were geo-targeted by area code.
“The texts were sent in bursts with varying bank affiliations, including Bank of America, Fifth Third Bank, and Susquehanna Bank,” he said. “The campaign last week was an identical case to one a week or so earlier that referenced Key Bank, Bank of America and Wells Fargo.”
Numbercop says the text message lures were sent using email-to-SMS gateways, but that the company also has seen similar campaigns sent from regular in-network numbers (prepaid mobile phones e.g.), which can be harder to catch. In addition, Volzke said, phishers often will target AT&T and Verizon users for use in furthering these schemes.
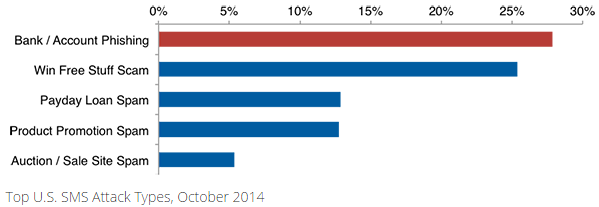
Many banks now offer their customers the ability to receive text message alerts about activity on their credit card accounts — such as recent transactions — so it’s not surprising that crooks are exploiting this medium. While vishing and SMiShing attacks are not new (see this story from 2010), they are on the rise: According to Cloudmark, the incidence of SMS bank account phishing in the U.S. more than tripled in September 2014. Cloudmark’s recently released Annual Threat Report found more than one in four unsolicited SMS messages reported in 2014 attempted to steal the victim’s personal or financial information.
Volzke says it’s unfortunate that more financial institutions aren’t communicating with their customers via mobile banking apps.
“Banking apps are among the most frequently downloaded and used apps,” Volzke said. “If the user has an app from the bank installed, then if the bank really has something to say they should use the in-app messaging method, not text messages which can be spoofed and are not secure. And yet we see almost no bank making use of this.”
Regardless of whether you communicate with your bank via text message, avoid calling phone numbers or clicking links that appear to have been sent via text message from your bank. Also, be extremely wary of any incoming calls from someone calling from your bank. If you think there may be an issue with your account, your best bet is to simply call the number on the back of your credit or debit card.