Chipotle Serves Up Chips, Guac & HR Email
lundi 16 novembre 2015 à 23:51The restaurant chain Chipotle Mexican Grill seems pretty good at churning out huge numbers of huge burritos, but the company may need to revisit some basic corporate cybersecurity concepts. For starters, Chipotle’s human resources department has been replying to new job applicants using the domain “chipotlehr.com” — a Web site name that the company has never owned or controlled.
 Translation: Until last week, anyone could have read email destined for the company’s HR department just by registering the domain “chipotlehr.com”. Worse, Chipotle itself has inadvertently been pointing this out for months in emails to everyone who’s applied for a job via the company’s Web site.
Translation: Until last week, anyone could have read email destined for the company’s HR department just by registering the domain “chipotlehr.com”. Worse, Chipotle itself has inadvertently been pointing this out for months in emails to everyone who’s applied for a job via the company’s Web site.
This security oversight by Chipotle was brought to light by KrebsOnSecurity.com reader Michael Kohlman, a professional IT expert who discovered the bug after applying for a job at the food retailer.
Kohlman, who’s between jobs at the moment, said he submitted his resume and application to Chipotle’s online HR department not necessarily because he wanted to be a restaurant employee, but more to satisfy the terms of his unemployment benefits (which require him to regularly show proof that he is actively looking for work).
Kohlman said after submitting his resume and application, he received an email from Chipotle Careers that bore the return address @chipotlehr.com. The Minnesota native said he became curious about the source of the Chipotle HR email when a reply sent to that address generated an error or “bounce” message saying his missive was undeliverable.
“The canned response was very odd,” Kohlman said. “Rather than indicating the email didn’t exist, [the bounced message] just came back and said it could not resolve the DNS settings.”
A quick search for ownership records on the domain showed that it had never before been registered. So, Kohlman said, on a whim he plunked down $30 to purchase it.
The welcome message that one receives upon successfully submitting an application for a job at Chipotle discourages users from replying to the message. But Kohlman said a brief look at the incoming email associated with that domain revealed a steady stream of wayward emails to chipotlehr.com — mainly from job seekers and people seeking password assistance to the Chipotle HR portal.
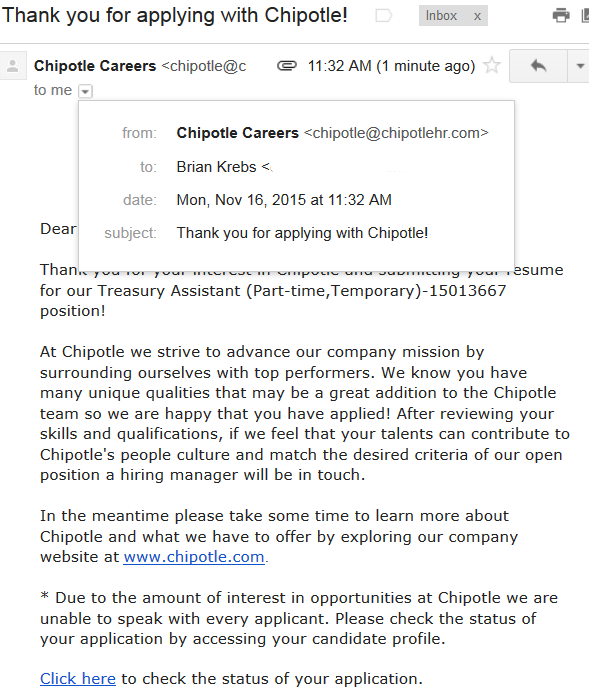
A confirmation letter I got from Chipotle Careers, which for at least several months used the reply address chipotlehr.com, a domain the company didn’t own.
“In nutshell, everything that goes in email to this HR system could be grabbed, so the potential for someone to abuse this is huge,” said Kohlman. “As someone who has made a big chunk of their career defending against cyber-attackers, I’d rather see Chipotle and others learn from their mistakes rather than cause any real damage.”
Kohlman has since offered to freely give over the domain to the restaurant chain. But Chipotle expressed zero interest in acquiring the free domain. In fact, Chipotle’s spokesman Chris Arnold says the company doesn’t see this as a big deal at all.
“The chipotlehr.com domain is not a functional address and never has been,” Arnold wrote in an emailed statement. “It never had any operational significance, and never served to solicit or accept any kind of response. So there has never been a security risk of any kind associated with this. That address is being changed to careers.chipotle.com (a domain that we do own), but this has never been functional and is really a non-issue.”
I suppose that’s not really a shocking response from a $3.5 billion/year company that only just last month hired its first chief information officer. Chipotle still doesn’t have a job position that puts anyone in charge of computer security. One might say the company’s infosec security maturity level leaves a bit to be desired.
This entire debacle reminds me of a story I wrote for The Washington Post in 2008 titled “They Told You Not To Reply“. That piece was about an adventuresome young man who gamely registered the domain “donotreply.com” — just to see how badly the domain was being abused. Little did he know what he was signing up for: a constant glut of email destined for companies that had dumped customers there for years — including banks, defense contractors and a whole mess of other organizations that should have known better. He ending up publishing the funniest emails on his blog, and would usually only remove the emails after the offending companies agreed to make a donation to any local animal shelter.